
ebpf
eBPF 101: Your First Step into Kernel Programming
eBPF has revolutionized Linux observability and security by allowing sandboxed programs to run in the kernel without changing kernel source code or loading modules


ebpf
eBPF has revolutionized Linux observability and security by allowing sandboxed programs to run in the kernel without changing kernel source code or loading modules

networking
Learn how to leverage Wireshark’s powerful features for effective network analysis and security monitoring

security
Linux powers an estimated 90% of the cloud workload worldwide. Linux-based servers are an engineer's favorite when it comes to developing world-class products. But the idea that Linux is inherently secure is a common misconception. In 2022 alone there were around 1.7 million new Linux malware samples.

API
LiveAPI makes it easy to find any API endpoint in seconds with a quick search, even across messy or undocumented systems. Stop wasting time hunting for APIs — ship features faster by building on what already exists.

security
Dive into one of the most complex malware ever written, which affected more than 10 countries and even nuclear power plants. This industrial-grade attack was one of the first of its kind. Here is a small exploration of how it works and the history behind it.

liveapi
Selecting a framework for your SaaS can be quite challenging. Worry no more because after reading this article you will get an overall idea of what to use for your next MVP.

liveapi
LiveAPI is an AI-powered automated documentation solution. This is the second blog in the LiveAPI devlogs series

ai
Imagine real-time, interactive API docs that update directly from your codebase. LiveAPI is an AI-powered solution designed to remove the effort of traditional API documentation.

liveapi
In this article, we will explore essential metrics for enhancing your API documentation and setting up analytics to monitor live user interactions with APIs. Learn how to optimize your documentation and provide a better user experience
ai
Are you tired of working with API docs and taking days to build solutions? Do you wish you had a way to make your work fast and easy and give your team more time to focus on other tasks.
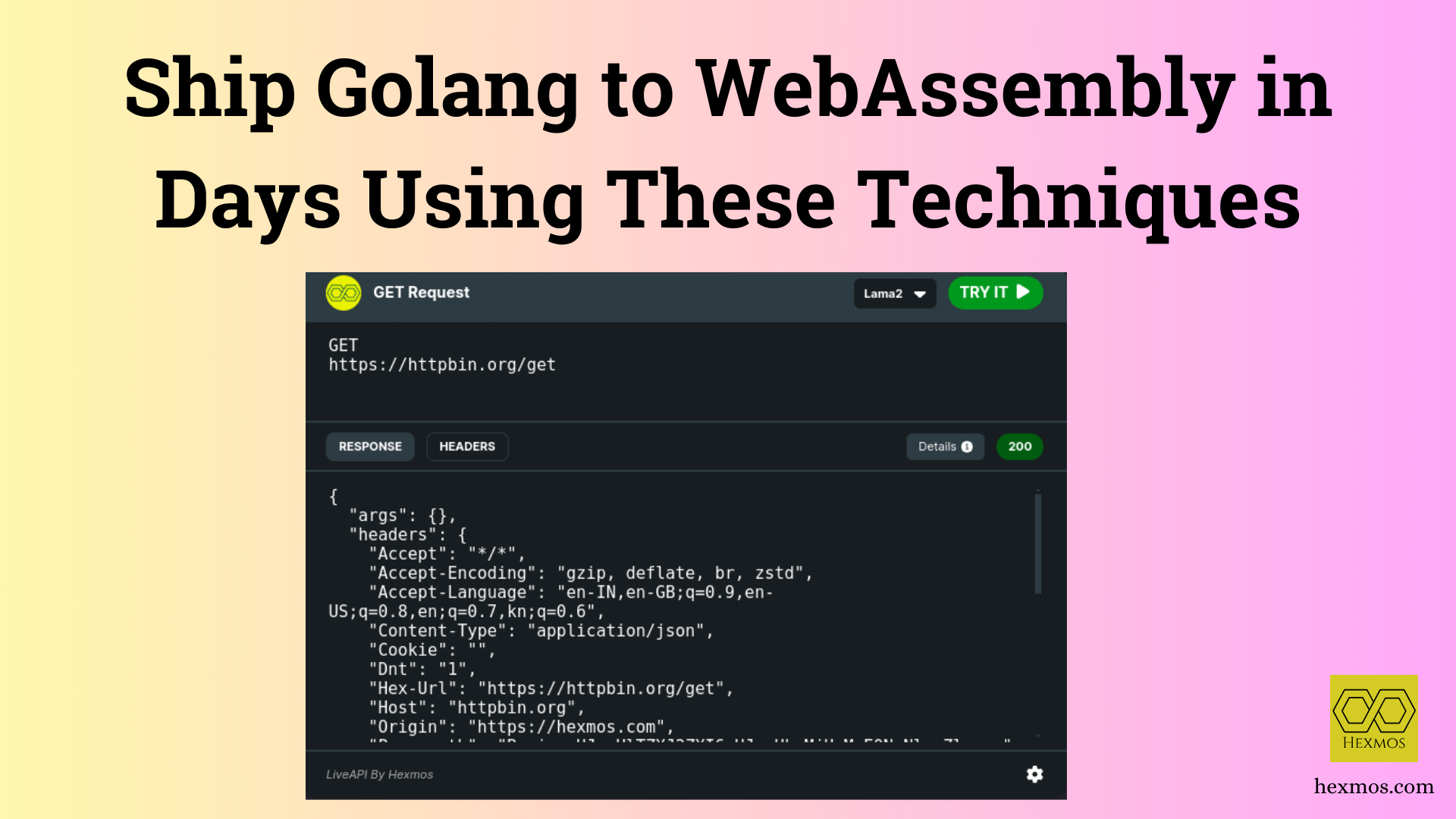
WASM
Have you ever tried to convert GoLang projects to WebAssembly? Follow along the journey on how to do it, and fix the painful roadblocks while you undergo the process.

ctfs
In this article, we explore how top cybersecurity hackers acquire their skills. You will also learn how you can develop these abilities and reach their level.